On This Page: [hide]
The next generation of VPNs is ushering in a new era of online privacy, connectivity, and performance, revolutionizing how we navigate the digital landscape. From enhanced security protocols to user-centric interfaces, these advanced VPN solutions are redefining the boundaries of what’s possible.

What Is a Next Gen VPN?
The Next Gen VPN represents an advancement in both network architecture and VPN technology, delivering an elevated level of control that translates to enhanced security for accessing a combination of cloud-based and centralized network resources, or even a hybrid amalgamation of the two.
Why Is There a Need for Next Gen VPNs?
Current challenges and inquiries frequently encountered today extend beyond the capabilities of conventional VPN technology.
Some of these issues encompass securely sharing data with external parties and contractors while averting data loss or breaches, fortifying remote and mobile workforce security, delivering a genuinely user-friendly remote access experience, ensuring secure, scalable communication with an array of remote IoT devices (e.g., cars, cameras), establishing secure connections among data centers and public/private cloud resources, and furnishing a secure link to hybrid cloud infrastructures. Although existing solutions offer workarounds and interim fixes for these scenarios, none comprehensively meet the criteria to be deemed an exemplary solution.
Traditional VPN technology effectively facilitates secure communication between remote locales and central servers, yet it falls short in providing the nuanced access control and robust support demanded by the prevalent usage of cloud applications integral to modern organizations. Particularly concerning enterprise entities, several factors underscore the imperative for Next Gen VPN technology:
- Elevated Risk Exposure Linked to Cloud Services. The adoption of cloud-based services exposes enterprises to heightened risk levels.
- Migration of Applications and Workloads to the Cloud. Applications and workloads continue their migration to various cloud models (PaaS, IaaS, SaaS).
- Threats Linked to Unrestricted Cloud Access. Unfettered entry to cloud storage and workloads poses a substantial peril.
- Pervasive Cloud Adoption. Private, public, and hybrid clouds all share sensitive enterprise data.
- Essentiality of Remote Access. A mobile workforce makes remote access an essential necessity, not just a desirable feature.
- Rapid Proliferation of IP-Connected Devices. The rapid proliferation of IP-connected devices contributes to the urgency.
- Rising Insider Threats and Insecure Infrastructure. Escalating internal security threats and the connection of legacy or insecure infrastructure to the internet, especially IoT devices, warrant attention.
- Shortage of IT and Security Expertise. A deficiency in IT and security expertise, specifically in automation and managed services, underscores the need for streamlined technology.
- Granular Access for External Parties. Enterprises must contend with the intricate task of granting access to contractors, suppliers, partners, customers, and developers. This necessitates partner identity management and more refined access control for third parties.
- Escalating Cyber Threats and IP Theft. The upsurge in cyber-attacks, malware, foreign exploitation, and intellectual property theft markedly compromises the security of remote access.
In view of these multifaceted challenges, the demand for Next Gen VPN technology becomes evident. The inherent limitations of conventional VPNs to adequately address these complexities fuel the necessity for a paradigm shift in VPN capabilities.
Next Gen VPN Technology Must-Haves
So, what should next gen VPNs offer to combat the technology’s current limitations?
Cutting-Edge Security Protocols
The cornerstone of next-gen VPNs lies in their adoption of cutting-edge security protocols. Traditional VPNs relied on established encryption methods, but the new generation is embracing protocols like WireGuard and ChaCha20, which offer improved performance and stronger security. WireGuard, for instance, utilizes modern cryptographic techniques, reducing latency and enhancing data transfer speeds while maintaining top-tier security. These protocols fortify the VPN’s ability to safeguard user data against emerging threats and potential vulnerabilities.
Zero-Trust Architecture
Next-gen VPNs are moving beyond conventional security paradigms by adopting a zero-trust architecture. This revolutionary approach challenges the assumption that users and devices within a network can be inherently trusted. Instead, all network traffic is treated as potentially malicious, requiring stringent authentication and authorization processes for access. By implementing zero-trust principles, these VPNs minimize the attack surface and significantly reduce the risk of unauthorized access or data breaches.
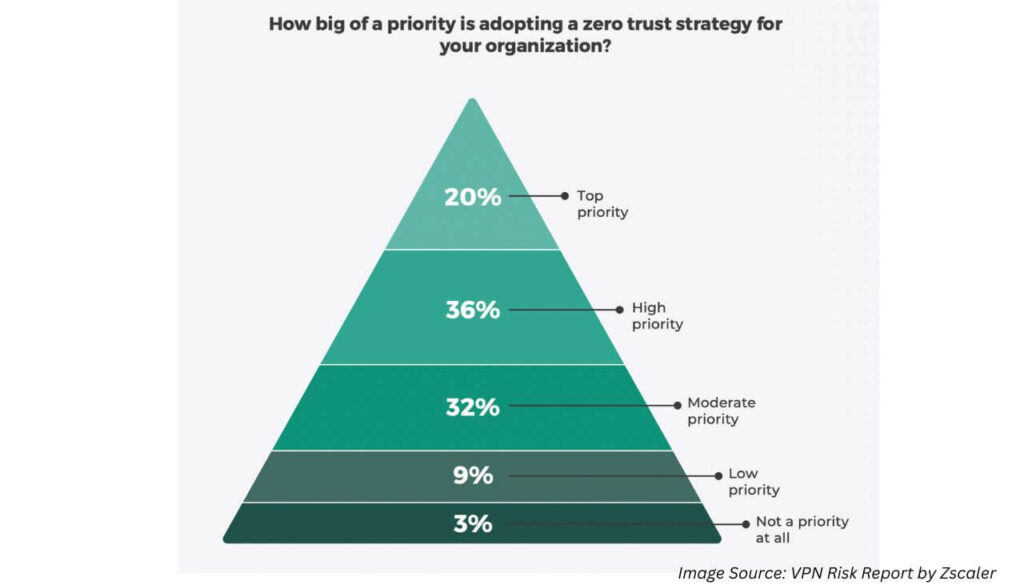
It is noteworthy that, according to a Zscaler VPN Risk Report, a substantial 92% of organizations (participants in the research) find themselves positioned within the spectrum of actions: either actively implementing (27%), currently in the planning stages (42%), or deeply considering a zero trust strategy. This collective stance underscores the widespread acknowledgment of the strategy’s importance and signifies the transition of zero trust from a mere buzzword to a concrete reality for the majority of enterprises.
Multi-Factor Authentication (MFA)
In the pursuit of ironclad security, next-gen VPNs leverage multi-factor authentication (MFA) as a fundamental layer of defense. MFA goes beyond the traditional username and password combination by requiring users to provide multiple forms of verification, such as biometrics, security tokens, or one-time codes. This approach adds an extra barrier against unauthorized access, making it significantly harder for attackers to compromise user accounts even if they obtain login credentials.
Server Infrastructure
The expansive server infrastructure of next-gen VPNs is a testament to their commitment to both security and accessibility. With servers strategically located across the globe, users gain the power to choose specific regions for routing their traffic. This not only enhances privacy by masking users’ true geographic locations but also allows users to bypass region-based content restrictions, granting them unfettered access to a world of online content.
Split Tunneling
Recognizing the diverse needs of users, next-gen VPNs introduce the concept of split tunneling. This feature enables users to direct only selected traffic through the VPN while letting other traffic access the internet directly. By doing so, users can optimize bandwidth usage, ensuring faster speeds for applications that require it, all while maintaining the security benefits of the VPN for sensitive activities.
Adaptive Routing and Load Balancing
The efficiency of next-gen VPNs is further underscored by their adaptive routing and load balancing capabilities. These VPNs intelligently route traffic through the most efficient servers based on factors such as server load and latency. This dynamic approach enhances connection speeds and overall performance, ensuring users experience seamless and uninterrupted connectivity, even during peak usage times.
Privacy-Centric Features
Beyond the fundamental role of masking IP addresses, next-gen VPNs embrace a suite of privacy-centric features. These may include robust DNS leak protection, strict no-logs policies that prevent any user activity from being stored, and advanced malware blocking to shield users from potential threats. With these features, users can trust that their online activities remain private and protected from prying eyes.
Speed and Performance
One of the most notable achievements of next-gen VPNs is their commitment to providing high-speed connections without compromising security. Through optimized server networks, advanced encryption protocols, and efficient routing mechanisms, these VPNs cater to bandwidth-intensive activities such as streaming and online gaming, offering an unmatched online experience that seamlessly marries speed with security.
User-Friendly Interfaces
User experience takes center stage in the design of next-gen VPNs. Intuitive interfaces across various platforms, including desktop and mobile applications, make it easy for users to set up, connect to, and manage their VPN connections. The ability to switch servers effortlessly, coupled with real-time connection status information, empowers users to take full control of their online security without the need for technical expertise.
Automated Security Updates
The ever-evolving nature of cyber threats necessitates proactive measures to safeguard user data. Next-gen VPNs rise to the challenge by incorporating automated security updates. By regularly updating their security protocols and mechanisms, these VPNs ensure that users are shielded from the latest vulnerabilities and threats, minimizing the risk of potential breaches.
Cross-Platform Compatibility
In an increasingly interconnected world, next-gen VPNs offer comprehensive protection for all devices, regardless of the operating system. From smartphones and tablets to laptops and even routers, these VPNs are designed to seamlessly integrate with a wide array of platforms, enabling users to safeguard their privacy and security across their entire digital ecosystem.
Advanced Support
The transition to next-gen VPNs is made smoother through dedicated customer support services. Leading providers offer assistance for setup, troubleshooting, and addressing user queries through various channels. This ensures that users can confidently make the most of the advanced features offered by these VPNs and overcome any challenges they may encounter.
Conclusive Thoughts
In a digital landscape characterized by constant change, next-gen VPNs are spearheading a revolution in online security and connectivity. With their enhanced security protocols, user-centric design, and performance-driven features, these VPNs stand as a beacon of hope for a future where privacy and connectivity coexist harmoniously. As technology continues to evolve, the next generation of VPNs will undoubtedly remain at the forefront of safeguarding our digital identities and redefining how we experience the online world.







